Products
Directory
High performance and secure LDAP/X.500 Directory services.
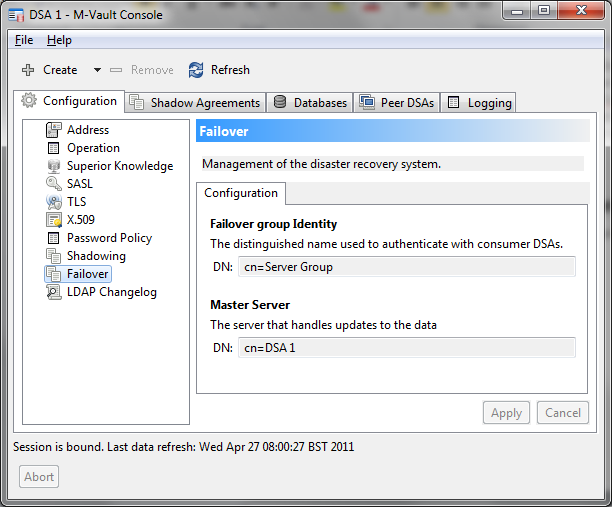
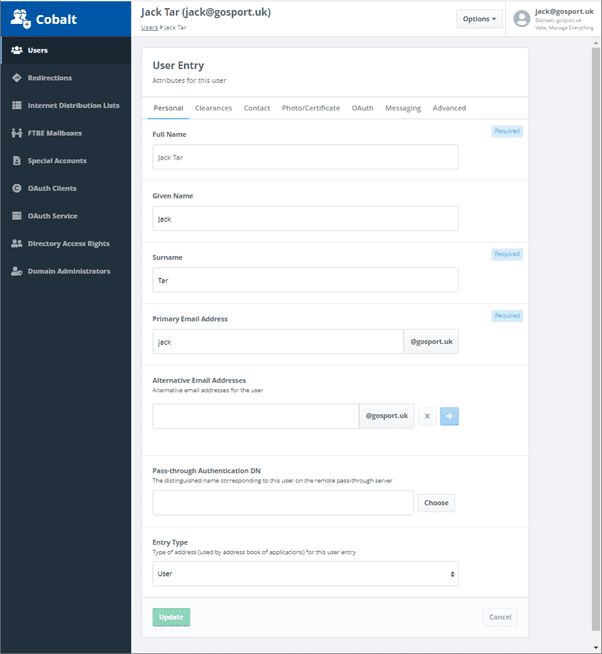
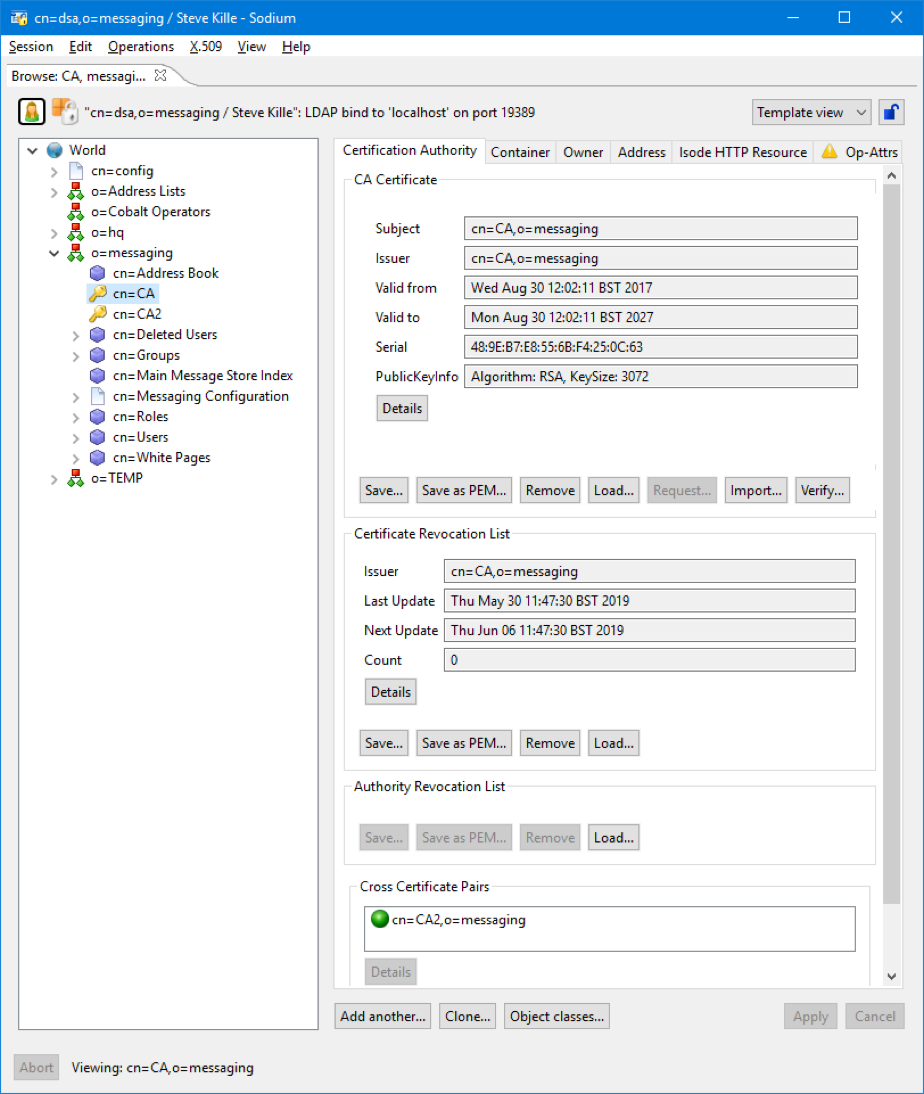
High Capacity X.500 Directories
HF Radio provides a critical backup option to more common communication networks, such as SatCom, but without modernisation they can’t do what you need. Our HF Network products provide the all important upgrades to turn an outdated comms system into a modern, reliable network.
High Performance
Access to information needs to be as quick as possible, your users don’t want to be waiting for a system to search through a slew of info to provide them what they need, that’s why we developed our directory products with high performance in mind. Our systems are designed to deliver the information users need as quickly as possible, no matter the size of your deployment.
Easily Scalable
Whether you’re looking for a small localised directory service, wanting to provide a directory for 2 million users, or anything in between, our systems are designed to scale with your requirements so that you can get the same quality service and high performance product regardless of the size requirements.
Open Standards
We but a lot of effort into making sure that our products are built with Open Standards in mind, and our directory software is no different. We have a long list of open standards compliance within our X.500 directory, this helps ensure that what we offer is not just a high quality product but it is designed with the end users in mind.
Read the latest Directory Whitepapers

Ready to request an Evaluation?
We welcome evaluations of our products and will make support resources available to you for the duration of your evaluation.