Directory
Cobalt
User & Role Provisioning
Cobalt provides a web interface for provisioning users, roles and other information in an LDAP directory. It enables easy addition and management of information to support directory white pages, XMPP deployments, email deployments and military messaging deployments.
Further details on this are provided in the whitepaper Provisioning for Military Messaging Handling Systems.
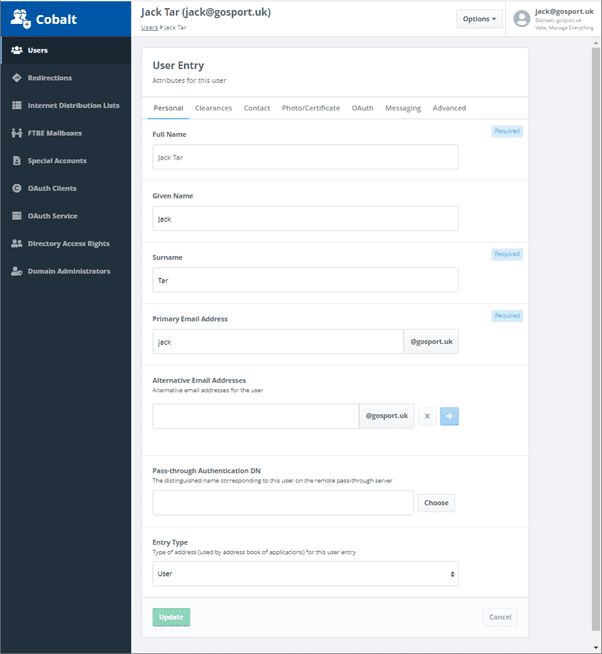
Users
A core Cobalt service is to provision users. This can be in support of XMPP, email or military messaging services or simply as a generic white pages provisioning to provide directory lookup and support by other applications.

Cobalt features comprehensive user management capabilities, in an easy to navigate interface. Administrators will have the ability to:
- Create new users
- Assign and reset passwords
- Delete, restore and purge users
- Lock accounts
- View and edit white pages information, including contact information and pictures
- Manage user X.509 PKI Certificates
Email & XMPP Support
Provisioned users may be configured as XMPP users and a special directory attribute may be used to identify the user. Users may also have a standard email address to support email service in conjunction with servers such as Isode M-Box.
For email usage, Cobalt also supports provisioning of redirections (e.g., for roles such as postmaster) and mailing lists.
Military Messaging Support
Cobalt provides a range of capabilities to support Formal Military Message Handling Systems (MMHS), with capabilities oriented towards support of systems using Isode’s Harrier, M-Box and M-Switch products. Capabilities provided include:
- Role based User Agents: A key characteristic of MMHS is that mailboxes are role based, with multiple users able to access a role and users able to access multiple mailboxes. Cobalt enables configuration of role based mailboxes (UAs).
- ACP 127 Support: UAs can be configured with ACP 127 attributes (RI and PLA) and also with line length, character set (ITA2/IA5) and attachment restrictions. Harrier will enforce these restrictions, which is important for messages that are transmitted using ACP 127.
- Option to configure STANAG 4406 Addresses.
- Capability Checking. Configuration of additional message capabilities of maximum message size and control of S/MIME signing/encryption.
- Military Address Lists. Military address lists are similar to email address lists, but list members are split into Action and Info recipients, in support of MMHS processing. Recipient configuration follows ACP 133 schema.
- Organizations (Profiled Addresses). MMHS messages flow between organizations. On message reception a message is sent to a Profiler, such as Isode’s M-Switch profiler which distributes the message to role based mailboxes. Cobalt allows provision of such profiled addresses that represent organizations. It also allows configuration of which roles are allowed to send messages on behalf of an organization, which Harrier picks up and presents valid choices to the role. In particular there is SIC (Subject Information Code) support with flexible profile configuration and SIC coverage.
- Draft & Release. For an Organization, Harrier can configure the draft and release rights of roles. Further information is provided in the Isode whitepaper [Isode’s Draft, Review & Release Solution].
- Organization/Role address type. To facilitate Harrier communication between Roles (for some functions) and Organizations (for released messages), Cobalt enforces User/Role/Organization type on managed entities. This is important, as it enables a distribution list to contain organizations only (or roles only) and then appear in address book as an organization (or role).
Security Management
Cobalt provides a range of capabilities for managing security information associated with users, roles and other entities. In particular:
- A range of support for user passwords including:
- Administrator assignment of passwords.
- User password management/reset
- Administrator email passwords to users
- Password policy support, including password quality and requiring user reset of new passwords.
- Security Clearances. Administrator assignment of security clearance to users and roles.
- 509 Certificates. Support for managing certificates including:
- S/MIME certificates for users
- Certificates for Isode servers
- HSM (Hardware Security Module) support
- CSR (Certificate Signing Request) generation.
- Directory Rights. Assignment of users to groups conferring directory access rights.
- OAuth Rights. Assigning rights to users for Isode applications using OAuth authorization.
As well as managing security information associated with users and roles, Cobalt provides capabilities for managing Isode Servers.
M-Vault Bootstrap
Cobalt facilitates headless M-Vault initial configuration by enabling server bootstrap with an initial user assigned to directory manager role.
Isode Server Support
Cobalt provides generic support for managing identities associated with Isode servers, in particular:
- Password management for servers using password authentication.
- Certificate and identity management for servers using PKI based strong authentication.
Hardware Security Modules (HSM)
Cobalt provides management capabilities for Hardware Security Modules (HSM):
- Initialization and test of multiple HSMs.
- Assigning default HSM.
- Support of HSM setup for Isode servers.
- Use of HSMs with S/MIME certificates for users and roles.
Support of Isode Applications using OAuth
Cobalt provides the capability to configure OAuth based authentication for Isode servers that use OAuth. This includes:
- Configuration of Isode’s OAuth server (part of M-Vault).
- Configuration of OAuth Clients representing Isode Web Applications that can use OAuth (currently Red/Black and Icon-5066)
- Configuration for each user of the rights (if any) they have to each OAuth Client.
This is described in more detail in the Isode [Isode OAuth] whitepaper.
M-Vault Core Server
Cobalt works with a primary M-Vault server, which holds Cobalt configuration. Commonly, this single directory server will also hold the data for all of the managed domains. For all configurations, a directory server needs to be present to hold Cobalt configuration information.
Replicated Directory Support
Where the M-Vault directory is replicated, multiple Cobalt instances may be configured to operate against it. This gives two benefits:
- In a distributed environment it is useful to have multiple Cobalt servers at different locations, each connected to the local node of a multi-master directory.
- Where a read only directory is replicated, for example using Sodium Sync to a Mobile Unit, it is useful to run Cobalt (read only) against the replica, to allow local administrators to conveniently view the configuration using Cobalt.
Active Directory Support
For a domain supporting users only, Cobalt can access Microsoft Active Directory with no schema changes. For such a domain, Cobalt cannot add or modify users, but can view the users that are configured in Active Directory.
This setup is important for support of MMHS where users are provisioned in Active Directory. Cobalt can then be used to configure Role Based UAs, where the role occupants are users configured in Active Directory. This enables use of Cobalt for MMHS configuration, while using Active Directory provisioned users and authentication.
Deleted Users
Deleted users entries are moved into a separate part of the directory to active users, which enables deleted users to be restored. This allows all Cobalt configured users to be searched from a single point in the DIT which does not include deleted users.
Cobalt will warn when a new user’s email or XMPP address matches a deleted user, to avoid ambiguity about who the recipient should be for messages directed to that address.
Cobalt Server Access to Directory
Cobalt maintains role based access control, recording which roles a given user has access to. When a user authenticates, a user with single role will simply run with that role. A user with rights to multiple roles will be given a choice of roles.
Cobalt Administrator Roles
Cobalt has two role types:
- Cobalt Administrator: Full access to all Cobalt administrator functions.
- Cobalt Viewer: Can see Cobalt configuration, but no rights to modify.
A Cobalt Administrator can assign users from any domain to either of these roles. A user not assigned to one of these roles has no access to Cobalt configuration.
Domain Administrator Roles
For each domain created by Cobalt, the following role types are supported for each domain:
- Manage Everything: Full rights for the domain, including management of domain administrators.
- Users Manager: Can add, delete and modify users.
- Roles Manager: Can add, delete and modify other Cobalt managed information for the domain.
- Users and Roles Viewer: Can view information for the domain.
User Services
Cobalt’s primary purpose is directory administration. Cobalt provides two related tools for users:
- Directory Viewer. This enables users to access information in the directory managed by Cobalt. This uses anonymous access for user convenience.
- Directory update which uses authenticated access and allows users to update attributes selected by an administrator.
Ready to request an Evaluation?
Thankyou for considering Isode’s software products. To request an evaluation, please select the product(s) you are interested in, then fill out the enquiry form.
Select your Evaluation products:
Customer Portal
For access to our customer portal please login below.
If you are having trouble accessing the portal please contact our support team who will be happy to help.
Need help with your account? Contact us
